Notice: this Wiki will be going read only early in 2024 and edits will no longer be possible. Please see: https://gitlab.eclipse.org/eclipsefdn/helpdesk/-/wikis/Wiki-shutdown-plan for the plan.
Difference between revisions of "Jan 29-31 Provo F2F Agenda"
m (Jan 15-17 Provo F2F Agenda moved to Jan 29-31 Provo F2F Agenda) |
|||
| (307 intermediate revisions by 14 users not shown) | |||
| Line 1: | Line 1: | ||
| − | Higgins face-to-face meeting in Provo, Utah, January | + | Higgins face-to-face meeting in Provo, Utah, January 29-31, 2008. |
| − | + | == Logistics == | |
| − | The event will start Tuesday | + | * '''Location:''' Executive Briefing Room 1, Building H, Novell's office. 1800 South Novell Place, Provo, UT 84606, (801) 861-7000, [http://maps.google.com/maps?f=q&hl=en&geocode=&q=1800+Novell+Pl,+Provo,+UT+84606&sll=40.209737,-111.655571&sspn=0.002679,0.005005&ie=UTF8&t=h&z=16&om=0 map] |
| + | ** After you enter building H, the executive briefing rooms are through glass doors on your right. | ||
| + | ** Call Jim at 801 380 8760 if you have any problems. | ||
| + | * '''Time''': The event will start Tuesday at 9:00 AM and end Thursday at noon. | ||
| + | ** A continental breakfast will be available starting at 8:30 AM | ||
| + | ** For early-comers and late-leavers, we're planning one or more ski days. See the [http://www.doodle.ch/participation.html?pollId=vmwkdbedcypcrci3 ski poll] | ||
| + | * '''Hotel''': Several of us are staying at the Marriott Conference Center in Provo ([http://maps.google.com/maps?f=d&hl=en&geocode=&time=&date=&ttype=&saddr=101+West+100+North,+Provo,+UT&daddr=1860+South+100+E,+Provo,+UT&sll=40.215587,-111.652679&sspn=0.023497,0.057335&ie=UTF8&ll=40.221705,-111.658295&spn=0.02683,0.00447&om=1&source=embed Map]). There are also a few hotels within walking distance (may have to deal with snow though) | ||
| + | * '''Weather''': Dress warmly. It may be cold. | ||
| + | * '''Getting there''': Most people fly into the [http://www.slcairport.com SLC airport] and drive to Provo. Here are [http://maps.google.com/maps?f=d&hl=en&geocode=&time=&date=&ttype=&saddr=SLC+-+Salt+Lake+City+Intl+Airport&daddr=40.209905,-111.655694&mra=dme&mrcr=0&mrsp=1&sz=18&sll=40.209467,-111.655244&sspn=0.002679,0.005005&ie=UTF8&t=h&z=18&om=0 directions] from SLC International Airport to Novell. | ||
| − | + | == Expected Attendees == | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
# Dale Olds - Novell | # Dale Olds - Novell | ||
# Jim Sermersheim - Novell | # Jim Sermersheim - Novell | ||
# Mary Ruddy - SocialPhysics/Parity | # Mary Ruddy - SocialPhysics/Parity | ||
# Paul Trevithick - SocialPhysics/Parity | # Paul Trevithick - SocialPhysics/Parity | ||
| − | # Tony Nadalin - | + | # Tony Nadalin - Bandit |
# Tom Doman - Novell | # Tom Doman - Novell | ||
# Daniel Sanders - Novell | # Daniel Sanders - Novell | ||
# Phil Hunt - Oracle | # Phil Hunt - Oracle | ||
# Drummond Reed - Cordance/Parity | # Drummond Reed - Cordance/Parity | ||
| + | # Andy Hodgkinson - Novell | ||
| + | # Duane Buss | ||
| + | # Michael McIntosh - IBM | ||
| + | # Markus Sabadello - Parity | ||
| + | # Carl Binding - IBM | ||
| + | # Uppili Srinivasan - Oracle | ||
| + | # George Stanchev - Serena | ||
| + | # Anthony Bussani - IBM | ||
| − | == | + | Attending by Phone (888-457-5984, passcode 5849826). Alert us on #higgins IRC for agenda items you wish to join for: |
| − | + | # Brian Carroll - Serena | |
| − | * [[ | + | # Paula Austel - IBM |
| − | * Review of | + | # David Primmer - Google (for session on STS IdP + SAML IdP refactoring) |
| − | * Higgins | + | # Bruce Rich - IBM |
| + | # Greg Byrd - IBM (for configuration discussion, possibly more) | ||
| + | |||
| + | == Tuesday == | ||
| + | ===NOTES ON THE AGENDA PROCESS=== | ||
| + | The agenda as proposed on this wiki page is just a place to start. Usually we rearrange and adjust the topics as the meeting progresses. We take notes right in this wiki page. If a demo is included it is in the topic's title line "[DEMO]". If the topic can't be moved there should be a bullet. | ||
| + | |||
| + | We will track at least the agenda on the #Higgins IRC channel. If you wish to call in for an agenda item, please let us know on the #higgins IRC channel and we'll set up a conference bridge. The conference bridge number will be 888-457-5984, passcode 5849826 | ||
| + | |||
| + | === 9:00-9:20 Welcome, Introductions, Logistics [Jim, Paul, Mary, (Dale)] === | ||
| + | * Introductions | ||
| + | * Eclipse ground rules | ||
| + | * Logistics | ||
| + | ** We will post the current agenda item to #higgins | ||
| + | *** Need IRC Scribes: Mike and Jim volunteered | ||
| + | ** Will take notes onto this Wiki | ||
| + | *** Need Wiki Scribes (we'll decide per session) | ||
| + | |||
| + | === 9:30 [2:20 hrs] IdAS & IGF Design [Jim and Phil] === | ||
| + | * See [[2008 Provo F2F IdAS & IGF Design Session Notes]] | ||
| + | |||
| + | === 11:50 [15min] Higgins 1.0 Release Plans [Mary] === | ||
| + | * Review of [https://bugs.eclipse.org/bugs/buglist.cgi?query_format=advanced&short_desc_type=allwordssubstr&short_desc=&product=Higgins&target_milestone=1.0&long_desc_type=allwordssubstr&long_desc=&bug_file_loc_type=allwordssubstr&bug_file_loc=&status_whiteboard_type=allwordssubstr&status_whiteboard=&keywords_type=allwords&keywords=&bug_status=NEW&bug_status=ASSIGNED&bug_status=REOPENED&emailtype1=substring&email1=&emailtype2=substring&email2=&bugidtype=include&bug_id=&votes=&chfieldfrom=&chfieldto=Now&chfieldvalue=&cmdtype=doit&order=Reuse+same+sort+as+last+time&field0-0-0=noop&type0-0-0=noop&value0-0-0= 1.0 bug list] | ||
| + | *Status of IP Review – IP Log accepted | ||
| + | *Status of Release Review | ||
| + | **Have OK to hold review | ||
| + | **Tentatively scheduled for Feb 13 | ||
| + | **First drafts slides due 1/30 | ||
| + | **Final slides due 1/3 | ||
| + | **Final slides posted by EMO on 1/6 | ||
| + | **Can release if get OK at release review (no more waiting period) | ||
| + | **Possible Eclipse announcement date – Feb 20 | ||
| + | *Status of "graduation from incubation" review - Revisit this after complete Release Review and 1.1 planning | ||
| + | * [http://www.eclipse.org/projects/dev_process/eclipse-quality.php Eclipse Quality page] | ||
| + | |||
| + | == Lunch == | ||
| + | == 1pm Tuesday Afternoon == | ||
| + | |||
| + | === [15min] Introduction to Higgins [Paul] === | ||
| + | * As we move towards paying more attention to documentation and technical marketing of what we've already done, we need to find a way to divide Higgins into logical peices. | ||
| + | * Paul will introduce the new three layer model (See [[Solutions]]) | ||
| + | * Paul will then focus on the "new/old" bottom layer: (see [[Context Data Model]]) | ||
| + | |||
| + | === [10min] API Extensibility [Jim] === | ||
| + | * Now that we've decided to consider Higgins APIs "provisional" (see <insert link>) this issue is something that we can keep working on over time. | ||
| + | * Jim present requirements | ||
| + | ** Differing proposals are at [[IdAS API Extensibility]] | ||
| + | ** Are we going to use deprecation? | ||
| + | * We're pushing this beyond 1.0, and tentatively pushing this agenda topic to a later slot. | ||
| + | |||
| + | === [1hr] IdAS and the Higgins Data Model; Open Issues [Jim] === | ||
| + | * Background: [[Higgins Data Model]] | ||
| + | * Issues are tracked at [[Data Model Open Issues#General]] | ||
| + | ** Covered "mixed attribute values" and "Closed or Open Simple data types" but didn't really get a lot of resolution. | ||
| + | ** Still need to talk about other two issues | ||
| + | |||
| + | === 3:00pm 15 min break === | ||
| + | === 3:15pm [30min] HOWL and the Higgins Data Model; Proposed update [Paul] === | ||
| + | * For background, here is the existing howl:[[HOWL]] | ||
| + | * Review of proposed changes to higgins.owl: [[HOWL Update]] | ||
| + | * [[New higgins.owl]] | ||
| + | * [[Person.owl Example]] | ||
| + | |||
| + | === 4:10pm [15min] Higgins on Android [Tony, Paul] === | ||
| + | * IBM | ||
| + | ** IBM's CES Demo | ||
| + | * Parity | ||
| + | ** [5min] Parity's work | ||
| + | *** WebKit limitations | ||
| + | *** Javascript injection approach | ||
| + | *** Challenges/Issues | ||
| + | *** Wishlist | ||
| + | * Starting an Android work area within Higgins? | ||
| + | ** IP issues around Android | ||
| + | ** Contributions | ||
| + | |||
| + | === 4:20pm [10min] DEMO: Eclipse-based Selector [Mike] === | ||
| + | * Solution: [[Eclipse-based Selector Solution]] | ||
| + | * Installation on Windows with IE | ||
| + | * Sign in to RP site | ||
| + | |||
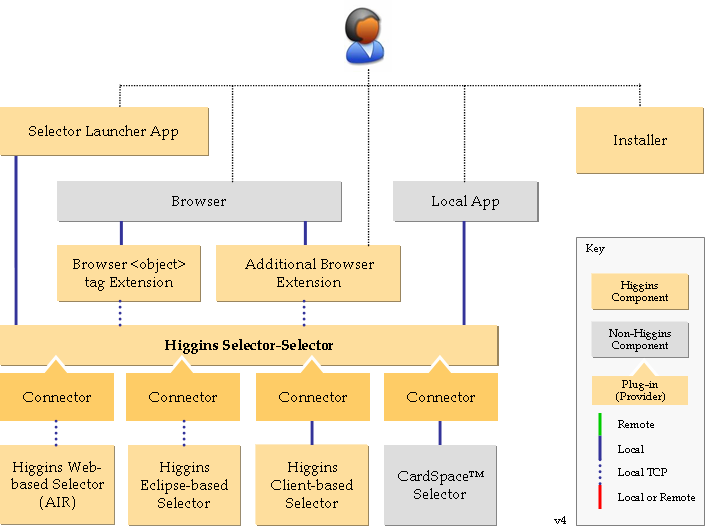
| + | === 4:30pm [45min+] Higgins Selector Selector [Mike, Paul] === | ||
| + | * Intro: Read http://www.incontextblog.com/?p=17 | ||
| + | * Platform-idependent architecture: [[Image:Hss-abstract-v4.PNG]] | ||
| + | * Discussion of the design | ||
| + | * See diagram on slide #7 here: <missing link> | ||
| + | * See also [[Higgins Platform Support]] notation proposal | ||
| + | |||
| + | === [5min] Report on Java Impl Selector Performance Issues [Paul] === | ||
| + | * [[Selector Performance Information]] | ||
| + | |||
| + | === [15min] DEMO: Client-based Selector "DigitalMe" [Andy] === | ||
| + | * Demo | ||
| + | * Current status | ||
| + | * Integration of next-gen HBX and Higgins Selector Selector ?? | ||
| + | * Documentation | ||
| + | ** Harmonization of Bandit site | ||
| + | * Roadmap | ||
| + | |||
| + | == 9:00am Wednesday Morning == | ||
| + | === 9:10 [10min] [DEMO] Firefox-embedded Selector Demo [Paul] === | ||
| + | * We've added what we think is a UI improvment over CardSpace UX: "remember this card (at this site)" (coupled with "remember this password for the card") | ||
| + | * [[Remember this Card Overview]] | ||
| + | * Feedback that something has happened when you use this feature | ||
| + | |||
| + | === 9:30 [45min] Selector UIs [Tony?, Andy?]=== | ||
| + | * Higgins is blessed(!) with multiple i-card selector UIs: | ||
| + | ** GTK-based "DigitalMe" on Linux | ||
| + | ** Cocoa-based "DigitalMe" on OSX | ||
| + | ** RCP-based | ||
| + | ** Firefox-embedded (requires hosted I-Card svc)h | ||
| + | ** AIR-based (requires hosted I-Card svc) | ||
| + | * Need to reduce the number of parallel implementations | ||
| + | * Need to converge on a common UI | ||
| + | ** Document the steps in '''any''' login process where: (trying for "common enough" here) | ||
| + | *** The user needs to make a decision (e.g. to operate a control) | ||
| + | *** What information is needed by the user to make the decision | ||
| + | *** Where this information comes from | ||
| + | *** What is at risk if such a choice is hidden from the user, e.g. by user preference | ||
| + | * Need to improve the UI | ||
| + | * What about http://wiki.eclipse.org/User_Interface_Best_Practices_Working_Group | ||
| + | |||
| + | === 10:15 [15 min] [DEMO] AIR-based Selector Demo [Jeesmon] === | ||
| + | * [3 min] HBX/Firefox Demo [Paul] | ||
| + | * [12 min] HBX/IE AIR web-based Selector Demo [Jeesmon remote from Needham, MA] | ||
| + | * Architecture Diagram including integration with Selector Selector | ||
| + | * Installation demonstration | ||
| + | * Login to RP site demonstration | ||
| + | |||
| + | === 10:30 [30min] The Future of the Configuration Component [Greg]=== | ||
* Configuration component: need two versions of Configuration.common (one for plugin-based configurations and one for jar-based configurations) | * Configuration component: need two versions of Configuration.common (one for plugin-based configurations and one for jar-based configurations) | ||
| − | * | + | * support "writing" not just reading |
| − | ** Merging | + | *# requirement: there's no configuration schema so I don't know how to build the Map |
| − | *** | + | *# requirement: ability to write out configuration |
| − | **** | + | *# requirement: ability to update the configuration itself through writing |
| − | **** use the | + | * better support for passwords in the file |
| − | ** Support for | + | * make it possible to do "round tripping" somehow (MikeM) |
| + | ** Mike please elaborate | ||
| + | * central configuration service? | ||
| + | ** problems: how to transfer stuff from file system (e.g. keystore) to the service? | ||
| + | ** we're currently passing objects around that are hard to serialize | ||
| + | ** use JSON | ||
| + | * Configuration UI? | ||
| + | * C++ Configuration Component? | ||
| + | |||
| + | === 11:00 [15 min] Access Control [Tom] === | ||
| + | * Access Control Issues in LDAP | ||
| + | * Acesss Control Issues in JNDI | ||
| + | * General Access Control Issues | ||
| + | * Providing Access Control through IdAS | ||
| + | * Should we start collecting use cases? | ||
| + | ** There is now [[Access_Control_in_IdAS]] | ||
| + | ** Tom and Jim will foster this | ||
| + | |||
| + | === 11:40 [20min] Separating out the Selector Authentication Service [Drummond]=== | ||
| + | * Today the web-based selector uses a username and "master" password to authenticate directly to the back end selector service (aka rpps) | ||
| + | * A new approach is to factor out provisioning and authentication of the client-side identity selector to separate web services. This approach has several advantages: | ||
| + | ** It can provide non-identifying tokens to provision and/or authenticate a back end selector service account, preserving privacy. | ||
| + | ** It can standardize provisioning and configuration of multiple front-end identity selectors (e.g., on different devices all used by the same user) to talk to the same back end identity agent. | ||
| + | ** It can opening new models of authentication in the future without requiring changes to the back end identity agent service. | ||
| + | * Work has begun on a protocol for this purpose: [[ISAP]] - Identity Selector Authentication Protocol. | ||
| + | * It lays the foundation for a "grand unification" of OpenID and Cards --The Selector Authentication Service can also (optionally) be the user's OpenID OP. We can nestle the concept of I-Cards UNDERNEATH the user's OpenID. OpenID's are great for public identification (e.g. log on to blogs, etc.) and for social networking and other low transaction value, public interactions where the person wants to use (or doesn't mind using) a 100% correlatable identifier. Cards are multiple, contextualized, nuanced and may be anonymous, pseudonymous, or partly to fully identifying. The opportunity here is to unify the two. Since the user already has an OpenID password at a service she trusts, we can (thanks to OpenID 1.1 and especially 2.0's XRDS discovery mechanism) simply add the Selector Service as a new XRDS service endpoint. The user now has only ONE master password. They have an OpenID that works anywhere and they have a card/selector service that integrates nicely with it. [Paul and Drummond are working on a white paper that describes this grand unification. The OpenID foundation is also exploring unification approaches, so this is all very timely] | ||
| + | * We have begun conversations with OpenID providers on implementing [[ISAP]] on their end to allow them to offer selector services | ||
| + | |||
| + | == Lunch == | ||
| + | === [15min] Review of Eclipse Release Review Slides [Mary] === | ||
| + | * Mary will send slides to list | ||
| + | |||
| + | == Wednesday Afternoon == | ||
| + | === [20 min] Considerations for a multi-protocol ID provider [Uppili] === | ||
| + | * When considering merging of STS and SAML from a Higgins infrastructure perspective, it will be useful to discuss and get some common understanding about what is the ultimate "functional" objective. Are there cross-functional use cases in scope for the resulting multi-protocol system, or are we just sharing code between what would be completely independent systems. Would this guide how to approach the same issue if a reference implementation of OpenID were considered as part of Higgins (in future). | ||
| + | ** Look at the canonical layers of an IDP | ||
| + | ** Allude about infrastructure building blocks that can be shared | ||
| + | ** Meditate about some cross-protocol use cases / scenarios (like global sign-out) | ||
| + | * ( I think this item should be here or somewhere prior to the "Merging" discussion, below). | ||
| + | |||
| + | === [15 min] Short session on STS IdP / SAML IdP merge/refactoring [Mike] === | ||
| + | * In NY we were looking at things that could be reused | ||
| + | * We agree it can be done | ||
| + | * To be continued on Thursday | ||
| + | |||
| + | === [15 min] Introduction to Open Identity Network Non-profit [Paul] === | ||
| + | * See [[OIN]] | ||
| + | * See http://openidentitynetwork.org <-- not "real" yet | ||
| + | * Status of incorporation/launch | ||
| + | |||
| + | === [30min] Introduction to R-Cards [Paul] === | ||
| + | * Evolution of i-card definition See http://en.wikipedia.org/wiki/I-card | ||
| + | * Definition of r-card. See [[R-Card]] --includes proposed ISIP-M-Card format extension/addition. | ||
| + | * Where r-cards fit in [[Higgins Data Model]] | ||
| + | * How they work -- the eCommerce change-of-address "VRM" use case | ||
| + | |||
| + | === [45min] Introduction to XDI and X3 [Drummond] === | ||
| + | * Very brief background on OASIS XDI TC | ||
| + | * Explain how XDI is the protocol equivalent of the [[Higgins Data Model]] (and that's why I'm working with Paul and Markus and Higgins) | ||
| + | * Show a few simple examples of X3 (using Markus' XDI Converter) to show how the [[XDI RDF Model]] can be used to implement the HDM and vice versa. | ||
| + | * Point out the [[XDI RDF Model]] sections. | ||
| + | * Finish by showing X3 for the same r-card scenario that Paul went through | ||
| + | |||
| + | === 3:45pm [15min] [DEMO] XDI4J Code Walk-through [Markus] === | ||
| + | * Introduce XDI4J | ||
| + | * Give a basic tour | ||
| + | * Show the XDI Messenger | ||
| + | * Show the XDI messages that would be transmitted for the BestBuy change of address VRM use case | ||
| + | |||
| + | === 4:10pm [45min] [DEMO] Novell open source IdP presentation [Daniel] === | ||
| + | * This uses the Higgins STS and IdAS components. Presentation will include the following: | ||
| + | * High level architectural overview of IdP and how Higgins STS and IdAS are used. | ||
| + | * Demonstration. | ||
| + | ** Download the IdP tarball. | ||
| + | ** Build it. | ||
| + | ** Deploy to server that has Tomcat installed. | ||
| + | ** Configure using web based admin. | ||
| + | *** Miscellaneous configuration. | ||
| + | *** Configuration of attributes that can be stored. | ||
| + | *** Configuration of information card templates. | ||
| + | *** Configuration of Java keystore | ||
| + | *** Configuration of IdAS context provider. | ||
| + | *** Look at the XML configuration files that are generated by admin. | ||
| + | *** Customizing how the IdP will look and feel. | ||
| + | ** Create user account | ||
| + | ** Manage user account, including change password | ||
| + | ** Issue information card using a card template | ||
| + | ** Use information card | ||
| + | |||
| + | === 5pm [45min] Design Principles [Mike] === | ||
| + | * Code Reuse and Size and Prerequisites | ||
| + | ** Reduce Download Size, Redundant Code, and Maintenance | ||
| + | ** Smallest/Earliest Possible JRE | ||
| + | * Reusable System Services | ||
| + | ** Configurable Components | ||
| + | *** Need to make the ConfigurationSettings available more consistently (getInstance/Singleton) | ||
| + | *** Need to convert classes in ...sts.utilities into shared components | ||
| + | ** ImplementationFactory | ||
| + | *** Code to Interfaces not Implementations | ||
| + | *** Configuration Maps Implementation Classes to Interfaces | ||
| + | *** Call "Object ImplementationFactory.getInstance(IInterfaceClass)" | ||
| + | ** ConversionService | ||
| + | *** Extensible by configuration, not by change to core code | ||
| + | *** Configuration Maps Conversion Classes to SourceClass/DestinationClass pairs | ||
| + | *** Replaces BindingHelper, CertificateHelper, XMLHelper, DateHelper, UUIDHelper, functions | ||
| + | *** Call "Object ConversionService.convert(Object from, Class to)" | ||
| + | *** Replace KeyGenHelper/X931KeyGenerator with: RPIDGenerator | ||
| + | **** CertificateChain should be passed in, should not reconnect in this module | ||
| + | > > PPIDGenerator | ||
| + | > > KeyPairGenerator | ||
| + | > > CertificateChainGenerator | ||
| + | > > UUIDGenerator | ||
| + | > > EVCertificateManager | ||
| + | > > Extensible by configuration | ||
| + | > > Call "boolean isEV(Certificate cert)", | ||
| + | > > WebApp Structure | ||
| + | > > Split TokenService WebApp into | ||
| + | > > TokenService (WS-Trust/STS) | ||
| + | > > MetadataExchangeService | ||
| + | > > ProfileService | ||
| + | > > All common code in JARs | ||
| + | > > All deployment specific configuration files +JARs in WAR | ||
| + | > > Move System Properties to WEB.XML file! | ||
| + | > > | ||
| + | |||
| + | === [15min] Plugin vs. JAR Dynamic Loading and ClassPath/Resource Issues [Mike] === | ||
| + | > > Can we add /Resource/*config.xml to Plugin without impact to | ||
| + | JARs? | ||
| + | > > How do we deal with log4j.properties? It is in the redist plugin | ||
| + | - | ||
| + | * how can we change it without changing plugin code? | ||
| + | |||
| + | === [30min] PKCS5 vs. ISO10126 Encryption/Decryption [Mike] === | ||
| + | Should always: Encrypt via PKCS5 and Decrypt via ISO10126 | ||
| + | Encrypt Decrypt | ||
| + | Relying Party No* Yes | ||
| + | Identity Selector Yes No* | ||
| + | Identity Provider Yes Yes | ||
| + | *Current implementations may not use encrypt or decrypt but future ones may. | ||
| + | The IXMLSecurityExtension should be broken into: | ||
| + | IXMLSignatureExtension | ||
| + | IXMLEncryptionExtension | ||
| + | IXMLDecryptionExtension | ||
| + | The xmlsecurity.apache should be broken into | ||
| + | xmlsignatureextension.apache | ||
| + | xmlencryptionextension.apache | ||
| + | xmldecryptionextension.apache | ||
| + | The xmlsec-1.4.0 (1.4.1) should not be in the redist plugin. | ||
| + | It should be in the various xml*extension.apache plugins. | ||
| + | The name of the config.xml (IBM vs. Sun(default)) should be a configuration setting | ||
| + | |||
| + | === 6:15 Dinner === | ||
| + | At Tucanos | ||
| + | 4801 North University Ave. | ||
| + | Unit 790 | ||
| + | Provo, Utah 84604 | ||
| + | [[http://maps.google.com/maps?f=d&hl=en&geocode=8989932769658583585,40.298778,-111.657776&saddr=40.209917,-111.655726&daddr=40.298778,-111.657776&mra=dme&mrcr=0&mrsp=0&sz=16&sll=40.208836,-111.653709&sspn=0.010062,0.016007&ie=UTF8&t=h&z=16&om=0 map]] | ||
| + | |||
| + | == Thursday == | ||
| + | === 9AM Agenda Bashing === | ||
| + | ===9:25 Data Model=== | ||
| + | Is defined by: | ||
| + | # HOWL based on OWL-FULL (with mods from what it is today) | ||
| + | # wiki/documents | ||
| + | Topics: | ||
| + | * Compare Tony's data model definitions with the wiki | ||
| + | |||
| + | === 10:33 Marketing & Outreach [Paul, Mary] === | ||
| + | * Bandit T-shirts Caroline Ford | ||
| + | * Communications Strategy | ||
| + | |||
| + | * DOOR 1 | ||
| + | ** Target audience: enterprise deployers, developers, and (in the long run) end users | ||
| + | ** Problem: I want a non-proprietary Identity Selector | ||
| + | ** Problem: I want an Identity Selector that runs on OSX or Linux | ||
| + | ** Solution: Higgins Identity Selector | ||
| + | *** Download one of the selectors | ||
| + | *** Get the source | ||
| + | |||
| + | * DOOR 2 | ||
| + | ** Target audience: Enterprise product consumers (deployment people) | ||
| + | ** Target audience: Open source developers | ||
| + | ** Problem: I want federated single-sign on solution | ||
| + | ** Problem: I want a non-proprietary Identity Selector | ||
| + | ** Problem: I want a non-proprietary IdP | ||
| + | ** Problem: I'm interested in WS-Trust-based identity technology | ||
| + | ** Solution: Higgins Identity Web Services | ||
| + | *** Try Eclipse-hosted demo services | ||
| + | *** Deploy your own server | ||
| + | *** Download the source | ||
| + | |||
| + | * DOOR 3 | ||
| + | ** Target audience: Open source developers | ||
| + | ** Problem: I'm interested in data portability (like the dataportability.org video) | ||
| + | ** Problem: Breaking down the identity silos | ||
| + | ** Solution: Context Data Model and the Higgins Global Graph | ||
| + | *** Download the spex | ||
| + | *** Look at the code | ||
| + | |||
| + | * State of the art evangelizing: [http://groups.google.com/group/dataportability-public/web/evangelism-projects-directory dataportability evangelism projects]. We should be so cool. They have a killer YouTube video (http://www.vimeo.com/610179) | ||
| + | ** Content (broken into the three Higgins layers layers) | ||
| + | *** Friendly, accessible descriptions of the problems | ||
| + | *** Sequence the content bottom layer to top (start with Higgins Global Graph) | ||
| + | *** A place to get key spex documents PDFs | ||
| + | ***# Relation & ContextId spex | ||
| + | ***# Higgins XRDS Service Endpoint | ||
| + | ***# HOWL and the Higgins Data Model | ||
| + | ***# Extensible ISIP-M-Card XML Format | ||
| + | ***# R-Card XML Format | ||
| + | * [Mary] Press release plan: coordination with Eclipse Foundation | ||
| + | * Discussion of how we will publicize Higgins 1.0. | ||
| + | * Outreach to independent OSS developers | ||
| + | ** What should we be doing? Should we have an plan? | ||
| + | ** What example CPs would get folks excited? A Twitter CP? | ||
| + | * Outreach to other related efforts | ||
| + | ** http://dataportability.org | ||
| + | ** http://www.opendatacommons.org/ | ||
| + | ** http://practicalportability.org/ | ||
| + | ** Semantic Web crowd | ||
| + | ** Etc | ||
| + | * Events | ||
| + | ** http://en.oreilly.com/et2008/public/content/home | ||
| + | ** http://www.eclipsecon.org/2008/ (March 17-20) | ||
| + | ** http://upcoming.yahoo.com/event/291704/ | ||
| + | ** http://webcamp.org/socialnetworkportability | ||
| + | ** http://en.oreilly.com/oscon2008/public/content/home | ||
| + | ** Etc. | ||
| + | |||
| + | === Release Planning, Roadmap === | ||
| + | |||
| + | |||
| + | ==== 1.0.0 (release) 20th of Feb ==== | ||
| + | * We'll create the 1.0 branch in the next few days | ||
| + | * We'll renumber all plugins to 1.0.0. | ||
| + | * Wiki page on how to configure the existing Jena CP using JDBC | ||
| + | |||
| + | ==== 1.0.1M1 (stable) Mid March PlugFest ==== | ||
| + | * WS-Trust 1.3, SOAP 1.2, etc. | ||
| + | * WS-Federation Passive Interop | ||
| + | * AIR-based selector, Higgins Selector Selector | ||
| + | * New Jena CP | ||
| + | * (Non-Jena) JDBC-based CP optimized for p/m-card storage | ||
| + | * De-Axisify | ||
| + | * Revised HOWL | ||
| + | |||
| + | ==== 1.0.1MX (stable) April 7-11 RSA ==== | ||
| + | * ISAP | ||
| + | * X509 | ||
| + | * Kerberos | ||
| + | * SAML 2.0 | ||
| + | |||
| + | ==== 1.0.1MX (stable) May 12-14 IIWa ==== | ||
| + | * WS-Federation Active Interop | ||
| + | |||
| + | ====1.0.1 (release) June ==== | ||
| + | * R-Cards | ||
| + | * OpenID | ||
| + | * Higgins Selector Selector | ||
| + | * UN/PW-Card | ||
| + | |||
| + | === Upcoming Interop Planning === | ||
| + | * RSA Conference | ||
| + | * Burton | ||
| + | * MSFT PlugFest (WS-Trust 1.3, SOAP 1.2, etc.) | ||
| + | ** NOTE: Need to Eliminate Axis | ||
| + | * WS-Federation Passive Interop | ||
| + | * WS-Federation Active Interop | ||
| + | * Objectives? | ||
| + | * Documentation of Higgins (eclipse-based, client-based, web-based) interop status/results? | ||
| + | ** The Higgins wiki is still circa June 2007 | ||
| + | ** Need a matrix of support for Higgins 1.0 | ||
| + | * New functionality | ||
| + | ** R-Cards | ||
| + | ** OpenID | ||
| + | ** Selector Selector | ||
| + | ** Managed Cards with X.509 for Authentication) | ||
| + | ** Managed Cards with Kerberos for Authentication | ||
| + | ** Username/Password Cards | ||
| + | ** Relying Party/STS | ||
| + | *** Cancel/Validate | ||
| + | *** Issuer Policy | ||
| + | ** Writable IdAS Interface for ProfileService | ||
| + | ** Support for Metadata on IdP and Client | ||
| + | ** OSGi Servlet Engine | ||
| + | |||
| + | == Thursday afternoon - Unofficial Continuation == | ||
| + | Whoever wants to stay, stay | ||
| + | |||
| + | ===12:20 More Higgins Data Model === | ||
| + | * continue working through definitions [[Higgins Data Model]] | ||
| + | |||
| + | === 1:30pm extensible ISIP-M format and CardStore === | ||
| + | * .crd ISIP-M <--making it extensible (.crdx??) | ||
| + | * .crd ISIP-P <--any changes?? | ||
| + | * .crds extensions | ||
| + | |||
| + | === 2pm [2hrs] STS IdP Solution in Depth [Mike]=== | ||
| + | * Similar to New York F2F sesion, but shorter | ||
| + | * (Weds or Thurs please) | ||
| + | * STS Work items: | ||
** STS token service still bypasses IdAS to access/update attributes | ** STS token service still bypasses IdAS to access/update attributes | ||
** Sample STS should cut over to using XMLFile Context Provider | ** Sample STS should cut over to using XMLFile Context Provider | ||
** Use of "informationCard generator" in STS's profile service? | ** Use of "informationCard generator" in STS's profile service? | ||
** Currently the STS MEX endpoint only advertises support for transport-level security (using UN token or self-seigned SAML token) | ** Currently the STS MEX endpoint only advertises support for transport-level security (using UN token or self-seigned SAML token) | ||
| − | * | + | |
| − | * | + | === OpenID and Oauth === |
| − | * | + | === [45min] Merging SAML2 IdP into STS framework [Mike, Markus] === |
| − | + | * Pre-merge refactoring | |
| − | * | + | ** Should we rename low level reusable sts.* components -> htp.* (Higgins Token Processing) |
| − | * | + | * Task planning |
| − | * | + | * Resources |
| − | ** | + | |
| − | ** | + | == Extra topics we might not get to == |
| − | ** | + | |
| − | * | + | |
| − | * | + | === [15 min] Card-based Oauth [Paul] === |
| − | ** | + | * Support for Oauth in the world of Higgins |
| − | ** | + | * Oauth uses redirects all over the place and asks the person to sign in using un/pw at the service |
| − | + | ||
| − | * | + | provider. There must be a better user experience. |
| − | * | + | * How about O-cards? User experience: |
| − | + | ** User gets an O-card from Service Provider (e.g. Google Calendar) | |
| − | **** | + | ** User fires up Oauth Consumer that wants Google Calendar data stream |
| − | * | + | ** Selector appears with Google Calendar card displayed |
| − | * | + | ** Selector UI asks to approve grant of rights |
| − | * | + | ** User clicks "Approve" button |
| − | * | + | ** Done. [No redirects, no un/pw entry at SP, etc.] |
| − | *** | + | |
| − | ** | + | === Autobuilds, Auto-tests === |
| − | ** | + | * Eclipse features building: Peter is working on this |
| − | ** | + | * C++: currently built using "cmake" (configure and make). compatible with SUSE autobuild service. |
| − | * | + | |
| + | builds the RPM packages. | ||
| + | * Nightly Junit tests: for longer term | ||
| + | |||
| + | === Moving, Renaming Components === | ||
| + | * Split selector selector from HBXIE | ||
| + | * Plugins folder | ||
| + | * .deployment.idas.basic -> move to app? | ||
| + | * .rpps -> ss | ||
| + | * .rsse -> rename to .ss.rsse | ||
| + | |||
| + | === [30min] Five ways to integrate OpenID [Paul] === | ||
| + | #OP Uses Cards for Auth (prevents phishing) | ||
| + | #Sxip OpenID Cards (OpenID claim type in managed cards or shared cards) | ||
| + | #OpenID Card: fills in pw at OP (prevents phishing) | ||
| + | #OpenID CP: OpenID OP into CP | ||
| + | #OpenID & Cards: Grand Unification | ||
| + | |||
| + | |||
| + | === More Fodder === | ||
| + | * [[Beyond Higgins 1.0]] | ||
| + | |||
| + | == Friday == | ||
| + | Skiing at The Canyons | ||
| + | * Plan is to meet at or around the Ticket Sales (#24 on [http://www.thecanyons.com/village_maps.html this page]) at 8:15AM, ready to ride | ||
| + | |||
| + | * Getting there: | ||
| + | ** [http://maps.google.com/maps?f=d&hl=en&geocode=3760309857024267151,40.557710,-111.425730&saddr=Novell+Pl,+provo,+ut&daddr=US-40+%4040.557710,+-111.425730+to:40.660848,-111.507111+to:4000+Canyons+Resort+Dr,+Park+City,+UT+84098+(Canyons+The)&mra=dpe&mrcr=0&mrsp=2&sz=10&via=1,2&sll=40.482425,-111.72918&sspn=0.608956,1.138458&ie=UTF8&z=10&om=0 shortest route] from Novell. | ||
| + | ** [http://maps.google.com/maps?f=d&hl=en&geocode=3760309857024267151,40.557710,-111.425730%3B4560409552164354824,40.663030,-111.500780&saddr=Novell+Pl,+provo,+ut&daddr=US-40+%4040.557710,+-111.425730+to:4000+Canyons+Resort+Dr,+Park+City,+UT+84098+(Canyons+The)&mra=mr&mrcr=0&via=1&sll=40.482425,-111.72918&sspn=0.608956,1.138458&ie=UTF8&z=10&om=0 slightly longer route] from Novell (not via Park City) | ||
| + | ** [http://maps.google.com/maps?f=d&hl=en&geocode=3760309857024267151,40.557710,-111.425730&saddr=Novell+Pl,+provo,+ut&daddr=4000+Canyons+Resort+Dr,+Park+City,+UT+84098+(Canyons+The)&mra=mr&mrcr=0&sll=40.482425,-111.72918&sspn=0.608956,1.138458&ie=UTF8&z=10&om=0 longer route] from Novell (most use of freeways) | ||
| + | ** Check [http://www.utahcommuterlink.com this site] for road conditions | ||
| + | * Expected attendees | ||
| + | # Carl Binding | ||
| + | # Phil Hunt | ||
| + | # Wendy Hunt | ||
| + | # Michael McIntosh | ||
| + | # Tony Nadalin | ||
| + | # Drummond Reed | ||
| + | # Markus Sabadello | ||
| + | # Jim Sermersheim | ||
| + | # Paul Trevithick | ||
== Links == | == Links == | ||
* [http://eclipse.org/higgins Higgins Home] | * [http://eclipse.org/higgins Higgins Home] | ||
Latest revision as of 20:57, 27 April 2008
Higgins face-to-face meeting in Provo, Utah, January 29-31, 2008.
Contents
- 1 Logistics
- 2 Expected Attendees
- 3 Tuesday
- 4 Lunch
- 5 1pm Tuesday Afternoon
- 5.1 [15min] Introduction to Higgins [Paul]
- 5.2 [10min] API Extensibility [Jim]
- 5.3 [1hr] IdAS and the Higgins Data Model; Open Issues [Jim]
- 5.4 3:00pm 15 min break
- 5.5 3:15pm [30min] HOWL and the Higgins Data Model; Proposed update [Paul]
- 5.6 4:10pm [15min] Higgins on Android [Tony, Paul]
- 5.7 4:20pm [10min] DEMO: Eclipse-based Selector [Mike]
- 5.8 4:30pm [45min+] Higgins Selector Selector [Mike, Paul]
- 5.9 [5min] Report on Java Impl Selector Performance Issues [Paul]
- 5.10 [15min] DEMO: Client-based Selector "DigitalMe" [Andy]
- 6 9:00am Wednesday Morning
- 6.1 9:10 [10min] [DEMO] Firefox-embedded Selector Demo [Paul]
- 6.2 9:30 [45min] Selector UIs [Tony?, Andy?]
- 6.3 10:15 [15 min] [DEMO] AIR-based Selector Demo [Jeesmon]
- 6.4 10:30 [30min] The Future of the Configuration Component [Greg]
- 6.5 11:00 [15 min] Access Control [Tom]
- 6.6 11:40 [20min] Separating out the Selector Authentication Service [Drummond]
- 7 Lunch
- 8 Wednesday Afternoon
- 8.1 [20 min] Considerations for a multi-protocol ID provider [Uppili]
- 8.2 [15 min] Short session on STS IdP / SAML IdP merge/refactoring [Mike]
- 8.3 [15 min] Introduction to Open Identity Network Non-profit [Paul]
- 8.4 [30min] Introduction to R-Cards [Paul]
- 8.5 [45min] Introduction to XDI and X3 [Drummond]
- 8.6 3:45pm [15min] [DEMO] XDI4J Code Walk-through [Markus]
- 8.7 4:10pm [45min] [DEMO] Novell open source IdP presentation [Daniel]
- 8.8 5pm [45min] Design Principles [Mike]
- 8.9 [15min] Plugin vs. JAR Dynamic Loading and ClassPath/Resource Issues [Mike]
- 8.10 [30min] PKCS5 vs. ISO10126 Encryption/Decryption [Mike]
- 8.11 6:15 Dinner
- 9 Thursday
- 10 Thursday afternoon - Unofficial Continuation
- 11 Extra topics we might not get to
- 12 Friday
- 13 Links
Logistics
- Location: Executive Briefing Room 1, Building H, Novell's office. 1800 South Novell Place, Provo, UT 84606, (801) 861-7000, map
- After you enter building H, the executive briefing rooms are through glass doors on your right.
- Call Jim at 801 380 8760 if you have any problems.
- Time: The event will start Tuesday at 9:00 AM and end Thursday at noon.
- A continental breakfast will be available starting at 8:30 AM
- For early-comers and late-leavers, we're planning one or more ski days. See the ski poll
- Hotel: Several of us are staying at the Marriott Conference Center in Provo (Map). There are also a few hotels within walking distance (may have to deal with snow though)
- Weather: Dress warmly. It may be cold.
- Getting there: Most people fly into the SLC airport and drive to Provo. Here are directions from SLC International Airport to Novell.
Expected Attendees
- Dale Olds - Novell
- Jim Sermersheim - Novell
- Mary Ruddy - SocialPhysics/Parity
- Paul Trevithick - SocialPhysics/Parity
- Tony Nadalin - Bandit
- Tom Doman - Novell
- Daniel Sanders - Novell
- Phil Hunt - Oracle
- Drummond Reed - Cordance/Parity
- Andy Hodgkinson - Novell
- Duane Buss
- Michael McIntosh - IBM
- Markus Sabadello - Parity
- Carl Binding - IBM
- Uppili Srinivasan - Oracle
- George Stanchev - Serena
- Anthony Bussani - IBM
Attending by Phone (888-457-5984, passcode 5849826). Alert us on #higgins IRC for agenda items you wish to join for:
- Brian Carroll - Serena
- Paula Austel - IBM
- David Primmer - Google (for session on STS IdP + SAML IdP refactoring)
- Bruce Rich - IBM
- Greg Byrd - IBM (for configuration discussion, possibly more)
Tuesday
NOTES ON THE AGENDA PROCESS
The agenda as proposed on this wiki page is just a place to start. Usually we rearrange and adjust the topics as the meeting progresses. We take notes right in this wiki page. If a demo is included it is in the topic's title line "[DEMO]". If the topic can't be moved there should be a bullet.
We will track at least the agenda on the #Higgins IRC channel. If you wish to call in for an agenda item, please let us know on the #higgins IRC channel and we'll set up a conference bridge. The conference bridge number will be 888-457-5984, passcode 5849826
9:00-9:20 Welcome, Introductions, Logistics [Jim, Paul, Mary, (Dale)]
- Introductions
- Eclipse ground rules
- Logistics
- We will post the current agenda item to #higgins
- Need IRC Scribes: Mike and Jim volunteered
- Will take notes onto this Wiki
- Need Wiki Scribes (we'll decide per session)
- We will post the current agenda item to #higgins
9:30 [2:20 hrs] IdAS & IGF Design [Jim and Phil]
11:50 [15min] Higgins 1.0 Release Plans [Mary]
- Review of 1.0 bug list
- Status of IP Review – IP Log accepted
- Status of Release Review
- Have OK to hold review
- Tentatively scheduled for Feb 13
- First drafts slides due 1/30
- Final slides due 1/3
- Final slides posted by EMO on 1/6
- Can release if get OK at release review (no more waiting period)
- Possible Eclipse announcement date – Feb 20
- Status of "graduation from incubation" review - Revisit this after complete Release Review and 1.1 planning
- Eclipse Quality page
Lunch
1pm Tuesday Afternoon
[15min] Introduction to Higgins [Paul]
- As we move towards paying more attention to documentation and technical marketing of what we've already done, we need to find a way to divide Higgins into logical peices.
- Paul will introduce the new three layer model (See Solutions)
- Paul will then focus on the "new/old" bottom layer: (see Context Data Model)
[10min] API Extensibility [Jim]
- Now that we've decided to consider Higgins APIs "provisional" (see <insert link>) this issue is something that we can keep working on over time.
- Jim present requirements
- Differing proposals are at IdAS API Extensibility
- Are we going to use deprecation?
- We're pushing this beyond 1.0, and tentatively pushing this agenda topic to a later slot.
[1hr] IdAS and the Higgins Data Model; Open Issues [Jim]
- Background: Higgins Data Model
- Issues are tracked at Data Model Open Issues#General
- Covered "mixed attribute values" and "Closed or Open Simple data types" but didn't really get a lot of resolution.
- Still need to talk about other two issues
3:00pm 15 min break
3:15pm [30min] HOWL and the Higgins Data Model; Proposed update [Paul]
- For background, here is the existing howl:HOWL
- Review of proposed changes to higgins.owl: HOWL Update
- New higgins.owl
- Person.owl Example
4:10pm [15min] Higgins on Android [Tony, Paul]
- IBM
- IBM's CES Demo
- Parity
- [5min] Parity's work
- WebKit limitations
- Javascript injection approach
- Challenges/Issues
- Wishlist
- [5min] Parity's work
- Starting an Android work area within Higgins?
- IP issues around Android
- Contributions
4:20pm [10min] DEMO: Eclipse-based Selector [Mike]
- Solution: Eclipse-based Selector Solution
- Installation on Windows with IE
- Sign in to RP site
4:30pm [45min+] Higgins Selector Selector [Mike, Paul]
- Intro: Read http://www.incontextblog.com/?p=17
- Platform-idependent architecture:
- Discussion of the design
- See diagram on slide #7 here: <missing link>
- See also Higgins Platform Support notation proposal
[5min] Report on Java Impl Selector Performance Issues [Paul]
[15min] DEMO: Client-based Selector "DigitalMe" [Andy]
- Demo
- Current status
- Integration of next-gen HBX and Higgins Selector Selector ??
- Documentation
- Harmonization of Bandit site
- Roadmap
9:00am Wednesday Morning
9:10 [10min] [DEMO] Firefox-embedded Selector Demo [Paul]
- We've added what we think is a UI improvment over CardSpace UX: "remember this card (at this site)" (coupled with "remember this password for the card")
- Remember this Card Overview
- Feedback that something has happened when you use this feature
9:30 [45min] Selector UIs [Tony?, Andy?]
- Higgins is blessed(!) with multiple i-card selector UIs:
- GTK-based "DigitalMe" on Linux
- Cocoa-based "DigitalMe" on OSX
- RCP-based
- Firefox-embedded (requires hosted I-Card svc)h
- AIR-based (requires hosted I-Card svc)
- Need to reduce the number of parallel implementations
- Need to converge on a common UI
- Document the steps in any login process where: (trying for "common enough" here)
- The user needs to make a decision (e.g. to operate a control)
- What information is needed by the user to make the decision
- Where this information comes from
- What is at risk if such a choice is hidden from the user, e.g. by user preference
- Document the steps in any login process where: (trying for "common enough" here)
- Need to improve the UI
- What about http://wiki.eclipse.org/User_Interface_Best_Practices_Working_Group
10:15 [15 min] [DEMO] AIR-based Selector Demo [Jeesmon]
- [3 min] HBX/Firefox Demo [Paul]
- [12 min] HBX/IE AIR web-based Selector Demo [Jeesmon remote from Needham, MA]
- Architecture Diagram including integration with Selector Selector
- Installation demonstration
- Login to RP site demonstration
10:30 [30min] The Future of the Configuration Component [Greg]
- Configuration component: need two versions of Configuration.common (one for plugin-based configurations and one for jar-based configurations)
- support "writing" not just reading
- requirement: there's no configuration schema so I don't know how to build the Map
- requirement: ability to write out configuration
- requirement: ability to update the configuration itself through writing
- better support for passwords in the file
- make it possible to do "round tripping" somehow (MikeM)
- Mike please elaborate
- central configuration service?
- problems: how to transfer stuff from file system (e.g. keystore) to the service?
- we're currently passing objects around that are hard to serialize
- use JSON
- Configuration UI?
- C++ Configuration Component?
11:00 [15 min] Access Control [Tom]
- Access Control Issues in LDAP
- Acesss Control Issues in JNDI
- General Access Control Issues
- Providing Access Control through IdAS
- Should we start collecting use cases?
- There is now Access_Control_in_IdAS
- Tom and Jim will foster this
11:40 [20min] Separating out the Selector Authentication Service [Drummond]
- Today the web-based selector uses a username and "master" password to authenticate directly to the back end selector service (aka rpps)
- A new approach is to factor out provisioning and authentication of the client-side identity selector to separate web services. This approach has several advantages:
- It can provide non-identifying tokens to provision and/or authenticate a back end selector service account, preserving privacy.
- It can standardize provisioning and configuration of multiple front-end identity selectors (e.g., on different devices all used by the same user) to talk to the same back end identity agent.
- It can opening new models of authentication in the future without requiring changes to the back end identity agent service.
- Work has begun on a protocol for this purpose: ISAP - Identity Selector Authentication Protocol.
- It lays the foundation for a "grand unification" of OpenID and Cards --The Selector Authentication Service can also (optionally) be the user's OpenID OP. We can nestle the concept of I-Cards UNDERNEATH the user's OpenID. OpenID's are great for public identification (e.g. log on to blogs, etc.) and for social networking and other low transaction value, public interactions where the person wants to use (or doesn't mind using) a 100% correlatable identifier. Cards are multiple, contextualized, nuanced and may be anonymous, pseudonymous, or partly to fully identifying. The opportunity here is to unify the two. Since the user already has an OpenID password at a service she trusts, we can (thanks to OpenID 1.1 and especially 2.0's XRDS discovery mechanism) simply add the Selector Service as a new XRDS service endpoint. The user now has only ONE master password. They have an OpenID that works anywhere and they have a card/selector service that integrates nicely with it. [Paul and Drummond are working on a white paper that describes this grand unification. The OpenID foundation is also exploring unification approaches, so this is all very timely]
- We have begun conversations with OpenID providers on implementing ISAP on their end to allow them to offer selector services
Lunch
[15min] Review of Eclipse Release Review Slides [Mary]
- Mary will send slides to list
Wednesday Afternoon
[20 min] Considerations for a multi-protocol ID provider [Uppili]
- When considering merging of STS and SAML from a Higgins infrastructure perspective, it will be useful to discuss and get some common understanding about what is the ultimate "functional" objective. Are there cross-functional use cases in scope for the resulting multi-protocol system, or are we just sharing code between what would be completely independent systems. Would this guide how to approach the same issue if a reference implementation of OpenID were considered as part of Higgins (in future).
- Look at the canonical layers of an IDP
- Allude about infrastructure building blocks that can be shared
- Meditate about some cross-protocol use cases / scenarios (like global sign-out)
- ( I think this item should be here or somewhere prior to the "Merging" discussion, below).
[15 min] Short session on STS IdP / SAML IdP merge/refactoring [Mike]
- In NY we were looking at things that could be reused
- We agree it can be done
- To be continued on Thursday
[15 min] Introduction to Open Identity Network Non-profit [Paul]
- See OIN
- See http://openidentitynetwork.org <-- not "real" yet
- Status of incorporation/launch
[30min] Introduction to R-Cards [Paul]
- Evolution of i-card definition See http://en.wikipedia.org/wiki/I-card
- Definition of r-card. See R-Card --includes proposed ISIP-M-Card format extension/addition.
- Where r-cards fit in Higgins Data Model
- How they work -- the eCommerce change-of-address "VRM" use case
[45min] Introduction to XDI and X3 [Drummond]
- Very brief background on OASIS XDI TC
- Explain how XDI is the protocol equivalent of the Higgins Data Model (and that's why I'm working with Paul and Markus and Higgins)
- Show a few simple examples of X3 (using Markus' XDI Converter) to show how the XDI RDF Model can be used to implement the HDM and vice versa.
- Point out the XDI RDF Model sections.
- Finish by showing X3 for the same r-card scenario that Paul went through
3:45pm [15min] [DEMO] XDI4J Code Walk-through [Markus]
- Introduce XDI4J
- Give a basic tour
- Show the XDI Messenger
- Show the XDI messages that would be transmitted for the BestBuy change of address VRM use case
4:10pm [45min] [DEMO] Novell open source IdP presentation [Daniel]
- This uses the Higgins STS and IdAS components. Presentation will include the following:
- High level architectural overview of IdP and how Higgins STS and IdAS are used.
- Demonstration.
- Download the IdP tarball.
- Build it.
- Deploy to server that has Tomcat installed.
- Configure using web based admin.
- Miscellaneous configuration.
- Configuration of attributes that can be stored.
- Configuration of information card templates.
- Configuration of Java keystore
- Configuration of IdAS context provider.
- Look at the XML configuration files that are generated by admin.
- Customizing how the IdP will look and feel.
- Create user account
- Manage user account, including change password
- Issue information card using a card template
- Use information card
5pm [45min] Design Principles [Mike]
- Code Reuse and Size and Prerequisites
- Reduce Download Size, Redundant Code, and Maintenance
- Smallest/Earliest Possible JRE
- Reusable System Services
- Configurable Components
- Need to make the ConfigurationSettings available more consistently (getInstance/Singleton)
- Need to convert classes in ...sts.utilities into shared components
- ImplementationFactory
- Code to Interfaces not Implementations
- Configuration Maps Implementation Classes to Interfaces
- Call "Object ImplementationFactory.getInstance(IInterfaceClass)"
- ConversionService
- Extensible by configuration, not by change to core code
- Configuration Maps Conversion Classes to SourceClass/DestinationClass pairs
- Replaces BindingHelper, CertificateHelper, XMLHelper, DateHelper, UUIDHelper, functions
- Call "Object ConversionService.convert(Object from, Class to)"
- Replace KeyGenHelper/X931KeyGenerator with: RPIDGenerator
- CertificateChain should be passed in, should not reconnect in this module
- Configurable Components
> > PPIDGenerator > > KeyPairGenerator > > CertificateChainGenerator > > UUIDGenerator > > EVCertificateManager > > Extensible by configuration > > Call "boolean isEV(Certificate cert)", > > WebApp Structure > > Split TokenService WebApp into > > TokenService (WS-Trust/STS) > > MetadataExchangeService > > ProfileService > > All common code in JARs > > All deployment specific configuration files +JARs in WAR > > Move System Properties to WEB.XML file! > >
[15min] Plugin vs. JAR Dynamic Loading and ClassPath/Resource Issues [Mike]
> > Can we add /Resource/*config.xml to Plugin without impact to JARs? > > How do we deal with log4j.properties? It is in the redist plugin -
- how can we change it without changing plugin code?
[30min] PKCS5 vs. ISO10126 Encryption/Decryption [Mike]
Should always: Encrypt via PKCS5 and Decrypt via ISO10126
Encrypt Decrypt
Relying Party No* Yes
Identity Selector Yes No*
Identity Provider Yes Yes
*Current implementations may not use encrypt or decrypt but future ones may.
The IXMLSecurityExtension should be broken into:
IXMLSignatureExtension
IXMLEncryptionExtension
IXMLDecryptionExtension
The xmlsecurity.apache should be broken into
xmlsignatureextension.apache
xmlencryptionextension.apache
xmldecryptionextension.apache
The xmlsec-1.4.0 (1.4.1) should not be in the redist plugin.
It should be in the various xml*extension.apache plugins.
The name of the config.xml (IBM vs. Sun(default)) should be a configuration setting
6:15 Dinner
At Tucanos 4801 North University Ave. Unit 790 Provo, Utah 84604 [map]
Thursday
9AM Agenda Bashing
9:25 Data Model
Is defined by:
- HOWL based on OWL-FULL (with mods from what it is today)
- wiki/documents
Topics:
- Compare Tony's data model definitions with the wiki
10:33 Marketing & Outreach [Paul, Mary]
- Bandit T-shirts Caroline Ford
- Communications Strategy
- DOOR 1
- Target audience: enterprise deployers, developers, and (in the long run) end users
- Problem: I want a non-proprietary Identity Selector
- Problem: I want an Identity Selector that runs on OSX or Linux
- Solution: Higgins Identity Selector
- Download one of the selectors
- Get the source
- DOOR 2
- Target audience: Enterprise product consumers (deployment people)
- Target audience: Open source developers
- Problem: I want federated single-sign on solution
- Problem: I want a non-proprietary Identity Selector
- Problem: I want a non-proprietary IdP
- Problem: I'm interested in WS-Trust-based identity technology
- Solution: Higgins Identity Web Services
- Try Eclipse-hosted demo services
- Deploy your own server
- Download the source
- DOOR 3
- Target audience: Open source developers
- Problem: I'm interested in data portability (like the dataportability.org video)
- Problem: Breaking down the identity silos
- Solution: Context Data Model and the Higgins Global Graph
- Download the spex
- Look at the code
- State of the art evangelizing: dataportability evangelism projects. We should be so cool. They have a killer YouTube video (http://www.vimeo.com/610179)
- Content (broken into the three Higgins layers layers)
- Friendly, accessible descriptions of the problems
- Sequence the content bottom layer to top (start with Higgins Global Graph)
- A place to get key spex documents PDFs
- Relation & ContextId spex
- Higgins XRDS Service Endpoint
- HOWL and the Higgins Data Model
- Extensible ISIP-M-Card XML Format
- R-Card XML Format
- Content (broken into the three Higgins layers layers)
- [Mary] Press release plan: coordination with Eclipse Foundation
- Discussion of how we will publicize Higgins 1.0.
- Outreach to independent OSS developers
- What should we be doing? Should we have an plan?
- What example CPs would get folks excited? A Twitter CP?
- Outreach to other related efforts
- http://dataportability.org
- http://www.opendatacommons.org/
- http://practicalportability.org/
- Semantic Web crowd
- Etc
- Events
Release Planning, Roadmap
1.0.0 (release) 20th of Feb
- We'll create the 1.0 branch in the next few days
- We'll renumber all plugins to 1.0.0.
- Wiki page on how to configure the existing Jena CP using JDBC
1.0.1M1 (stable) Mid March PlugFest
- WS-Trust 1.3, SOAP 1.2, etc.
- WS-Federation Passive Interop
- AIR-based selector, Higgins Selector Selector
- New Jena CP
- (Non-Jena) JDBC-based CP optimized for p/m-card storage
- De-Axisify
- Revised HOWL
1.0.1MX (stable) April 7-11 RSA
- ISAP
- X509
- Kerberos
- SAML 2.0
1.0.1MX (stable) May 12-14 IIWa
- WS-Federation Active Interop
1.0.1 (release) June
- R-Cards
- OpenID
- Higgins Selector Selector
- UN/PW-Card
Upcoming Interop Planning
- RSA Conference
- Burton
- MSFT PlugFest (WS-Trust 1.3, SOAP 1.2, etc.)
- NOTE: Need to Eliminate Axis
- WS-Federation Passive Interop
- WS-Federation Active Interop
- Objectives?
- Documentation of Higgins (eclipse-based, client-based, web-based) interop status/results?
- The Higgins wiki is still circa June 2007
- Need a matrix of support for Higgins 1.0
- New functionality
- R-Cards
- OpenID
- Selector Selector
- Managed Cards with X.509 for Authentication)
- Managed Cards with Kerberos for Authentication
- Username/Password Cards
- Relying Party/STS
- Cancel/Validate
- Issuer Policy
- Writable IdAS Interface for ProfileService
- Support for Metadata on IdP and Client
- OSGi Servlet Engine
Thursday afternoon - Unofficial Continuation
Whoever wants to stay, stay
12:20 More Higgins Data Model
- continue working through definitions Higgins Data Model
1:30pm extensible ISIP-M format and CardStore
- .crd ISIP-M <--making it extensible (.crdx??)
- .crd ISIP-P <--any changes??
- .crds extensions
2pm [2hrs] STS IdP Solution in Depth [Mike]
- Similar to New York F2F sesion, but shorter
- (Weds or Thurs please)
- STS Work items:
- STS token service still bypasses IdAS to access/update attributes
- Sample STS should cut over to using XMLFile Context Provider
- Use of "informationCard generator" in STS's profile service?
- Currently the STS MEX endpoint only advertises support for transport-level security (using UN token or self-seigned SAML token)
OpenID and Oauth
[45min] Merging SAML2 IdP into STS framework [Mike, Markus]
- Pre-merge refactoring
- Should we rename low level reusable sts.* components -> htp.* (Higgins Token Processing)
- Task planning
- Resources
Extra topics we might not get to
[15 min] Card-based Oauth [Paul]
- Support for Oauth in the world of Higgins
- Oauth uses redirects all over the place and asks the person to sign in using un/pw at the service
provider. There must be a better user experience.
- How about O-cards? User experience:
- User gets an O-card from Service Provider (e.g. Google Calendar)
- User fires up Oauth Consumer that wants Google Calendar data stream
- Selector appears with Google Calendar card displayed
- Selector UI asks to approve grant of rights
- User clicks "Approve" button
- Done. [No redirects, no un/pw entry at SP, etc.]
Autobuilds, Auto-tests
- Eclipse features building: Peter is working on this
- C++: currently built using "cmake" (configure and make). compatible with SUSE autobuild service.
builds the RPM packages.
- Nightly Junit tests: for longer term
Moving, Renaming Components
- Split selector selector from HBXIE
- Plugins folder
- .deployment.idas.basic -> move to app?
- .rpps -> ss
- .rsse -> rename to .ss.rsse
[30min] Five ways to integrate OpenID [Paul]
- OP Uses Cards for Auth (prevents phishing)
- Sxip OpenID Cards (OpenID claim type in managed cards or shared cards)
- OpenID Card: fills in pw at OP (prevents phishing)
- OpenID CP: OpenID OP into CP
- OpenID & Cards: Grand Unification
More Fodder
Friday
Skiing at The Canyons
- Plan is to meet at or around the Ticket Sales (#24 on this page) at 8:15AM, ready to ride
- Getting there:
- shortest route from Novell.
- slightly longer route from Novell (not via Park City)
- longer route from Novell (most use of freeways)
- Check this site for road conditions
- Expected attendees
- Carl Binding
- Phil Hunt
- Wendy Hunt
- Michael McIntosh
- Tony Nadalin
- Drummond Reed
- Markus Sabadello
- Jim Sermersheim
- Paul Trevithick