Notice: this Wiki will be going read only early in 2024 and edits will no longer be possible. Please see: https://gitlab.eclipse.org/eclipsefdn/helpdesk/-/wikis/Wiki-shutdown-plan for the plan.
Difference between revisions of "SAML2 IdP"
| Line 1: | Line 1: | ||
{{#eclipseproject:technology.higgins}} | {{#eclipseproject:technology.higgins}} | ||
| + | == Version 1.0 == | ||
| + | * This page describes the Higgins 1.0 SAML2 IdP Solution | ||
| + | * See [[SAML2 IdP 1.1]] for the version currently under development | ||
| + | |||
==Introduction== | ==Introduction== | ||
Revision as of 12:42, 3 July 2008
{{#eclipseproject:technology.higgins}}
Contents
Version 1.0
- This page describes the Higgins 1.0 SAML2 IdP Solution
- See SAML2 IdP 1.1 for the version currently under development
Introduction
The Higgins SAML2 IdP supports the SP-initiated SSO profile defined by SAML 2.0 specifications. Two parties are involved in this profile: A service provider (relying party, SP), and an identity provider (IdP). The SP offers protected services and relies on the IdP to authenticate users.
See SAML2 IdP Overview for a detailed description of the SAML2 IdP solution's functionality.
An instance of the SAML2 IdP is deployed at https://graceland.parityinc.net/saml2idp-test/.
End-User Perspective
Functionality
The SAML2 IdP allows users to sign in to SPs (relying parties) using their credentials at some IdP.
Setup
The end user does not have to set up anything. The process is triggered by the end user trying to sign in at a SP.
Deployer Perspective
See SAML2 IdP Deployment for a detailed description of how to download and deploy the SAML2 IdP.
Download
See http://wiki.eclipse.org/SAML2_IdP_Deployment#Obtain_.WAR_files.
Deploying
See http://wiki.eclipse.org/SAML2_IdP_Deployment#Deploy_the_web_applications_on_Tomcat.
Configuration
See http://wiki.eclipse.org/SAML2_IdP_Deployment#Configure_the_web_applications.
Developer Perspective
See SAML2 IdP Development for a detailed description of how to set up your development environment for the SAML2 IdP solution.
Architecture
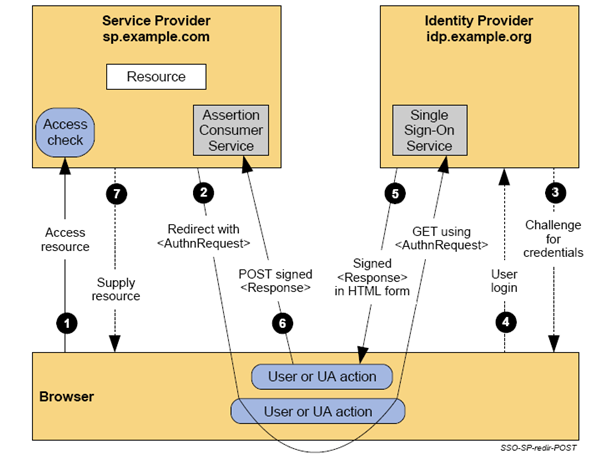
The SAML2 IdP solution consists of two web applications (the actual IdP, and an example SP). They support the SP-initiated SAML 2.0 SSO profile:
See http://www.oasis-open.org/committees/security/ for more details about the SAML 2.0 protocol.
The Higgins components used by this solution are:
- plugins/org.eclipse.higgins.configuration.api
- plugins/org.eclipse.higgins.configuration.common
- plugins/org.eclipse.higgins.configuration.xml
- plugins/org.eclipse.higgins.configuration.xrds
- plugins/org.eclipse.higgins.idas.api
- plugins/org.eclipse.higgins.idas.common
- plugins/org.eclipse.higgins.cp.jndi
- plugins/org.eclipse.higgins.idas.registry
- plugins/org.eclipse.higgins.idas.spi
- plugins/org.eclipse.higgins.messages
- plugins/org.eclipse.higgins.saml2idp.saml2
- plugins/org.eclipse.higgins.util.idas.cp
- plugins/org.eclipse.higgins.util.jscript
- plugins/org.eclipse.higgins.util.socket
Building
The two web applications that constitute the SAML2 IdP are:
- app/org.eclipse.higgins.saml2idp.server
- app/org.eclipse.higgins.saml2idp.test
These projects, as well as their dependencies, can be checked out from the Eclipse repository at the following SVN URI:
| svn://dev.eclipse.org/svnroot/technology |
Future Work
- SAML2 and STS Convergence covers ideas on how to integrate the SAML2 IdP Solution with the Higgins STS component.