Notice: this Wiki will be going read only early in 2024 and edits will no longer be possible. Please see: https://gitlab.eclipse.org/eclipsefdn/helpdesk/-/wikis/Wiki-shutdown-plan for the plan.
PDS 2.0
{{#eclipseproject:technology.higgins|eclipse_custom_style.css}}
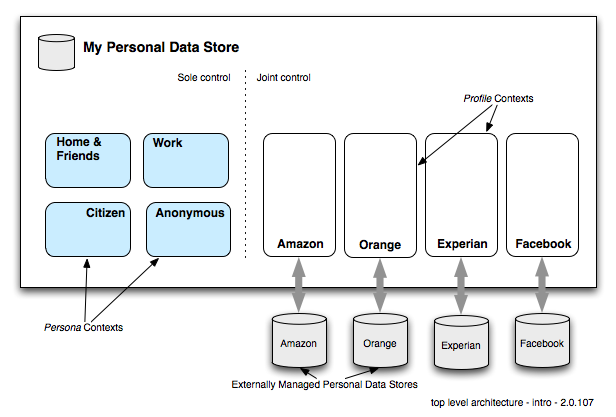
Within a PDS a single individual is represented as a set of Contexts each of which holds a digital identity called a Person. Each person instance has a set of attributes and values. Thus one individual (natural person, data subject) is represented as multiple Person entities each in its own context-container.
The data in these Contexts adheres to the Higgins Persona Data Model 2.0, which can be used for storing arbitrary (identity and social networking) data. UDI references are used for representing links between Contexts, both inside the Personal Data Store 2.0 and to external data stores.
Contents
Personal Data Store 2.0
Attribute data stored locally on the Personal Data Store 2.0 are encrypted on the client (identity agent) using a client-side key prior to transmission to the Personal Data Store 2.0. Thus data attribute values on the Personal Data Store 2.0 are blinded from the service operator offering/hosting the PDS service. PDS data may be accessed directly (as an endpoint) or via a PDS client library.
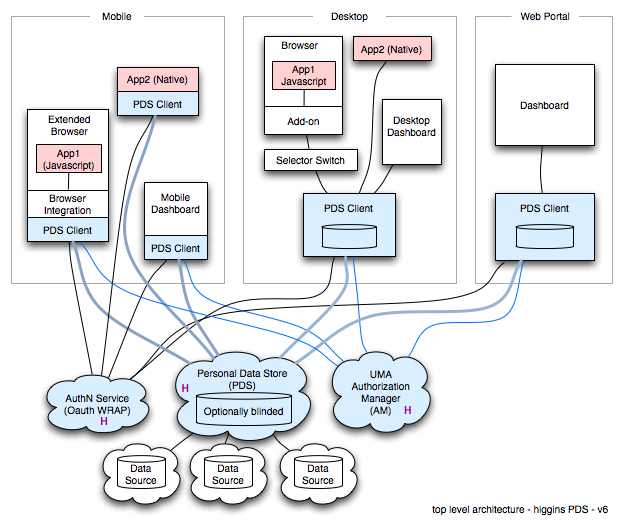
The blue areas of the following diagram are PDS-related:
The Personal Data Store 2.0 is a variant of the IdAS Proxy Service, with the following changes:
- The UDI Resolver is configured to support sync:// UDIs
- The IdAS Registry is configured to include the RDF2 Context Provider.
The IdAS Proxy Service is layered over the Attribute Service 1.1 to provide a bi-directional, synchronizing XDI endpoint over data managed by Context Provider plug-ins to the IdAS package. These context providers area also data adapters to a variety of back end data stores.
The Personal Data Store 2.0 can be accessed by:
- Sending XDI messages to its endpoint
- Using the following low level client libraries:
- Org.eclipse.higgins.idas.client (Java IdAS Client)
- Org.eclipse.higgins.idasclient.cpp.core (C++ IdAS Client)
- Using the PDS Client (under development)
PDS Client
The PDS Client 2.0 is code that apps may choose to use to access the Personal Data Store 2.0.
Authentication (AuthN) Service
The IdAS Proxy Service 2.0 and Attribute Service 2.0 require access tokens minted by the Authentication Service 2.0. Eventually the I-Card Service and CardSync Service will also rely on this external authN service.
Authorization Manager
- Authorization Manager (planned) gives the user control over the flows of data from a managed relationship card provider to a relying party. We plan to use/adapt Kantara UMA protocols.
Web Portal
- We plan to develop a Web Portal--an evolution of the Cloud Selector 1.1 from Higgins 1.1 with broader functionality.