Notice: this Wiki will be going read only early in 2024 and edits will no longer be possible. Please see: https://gitlab.eclipse.org/eclipsefdn/helpdesk/-/wikis/Wiki-shutdown-plan for the plan.
Difference between revisions of "EE4J Build"
(→Deployment to OSSRH / Maven Central) |
|||
| Line 16: | Line 16: | ||
Here are the required steps to configure your Jenkins build job for deployment to OSSRH: | Here are the required steps to configure your Jenkins build job for deployment to OSSRH: | ||
| − | + | {| class="wikitable" | |
| − | + | |- style="vertical-align:top;" | |
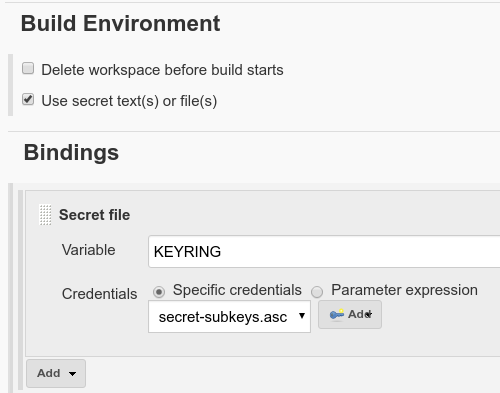
| − | + | |1. Insert <code>secret-subkeys.gpg</code> as secret file in job | |
| − | + | | [[File:InjectSecretFile.png]] | |
| − | + | |- style="vertical-align:top;" | |
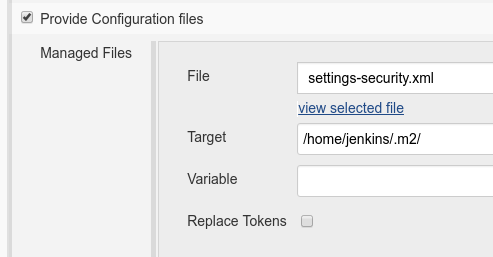
| − | + | |2. Inject <code>settings-security.xml</code> file into .m2 directory. The target must really be <code>/home/jenkins/.m2/settings-security.xml</code> and not <code>settings-security.xml</code> alone. | |
| + | <br/> | ||
| + | You can add it somewhere else, but you will need to add <code>-Dsettings.security=path/to/security-settings.xml</code> to every Maven invocation. | ||
| + | |[[File:InjectSettingsSecurity.png]] | ||
| + | |- style="vertical-align:top;" | ||
| + | |3. Import GPG keyring with <code>--batch</code> and trust the keys non-interactively in a shell build step<code> | ||
gpg --batch --import ${KEYRING} | gpg --batch --import ${KEYRING} | ||
for fpr in $(gpg --list-keys --with-colons | awk -F: '/fpr:/ {print $10}' | sort -u); | for fpr in $(gpg --list-keys --with-colons | awk -F: '/fpr:/ {print $10}' | sort -u); | ||
| Line 28: | Line 33: | ||
done | done | ||
</code> | </code> | ||
| − | + | | | |
| − | <code> | + | |- style="vertical-align:top;" |
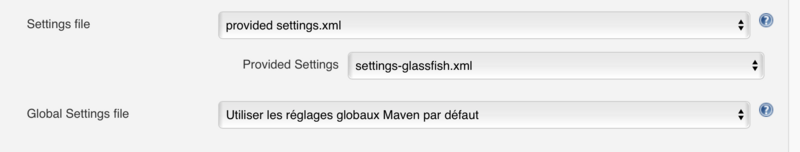
| + | |4. If you're using a Maven build step, just select the proper file. | ||
| + | <br/> | ||
| + | If you're using a Shell build step, inject <code>settings-<projectname>.xml</code> into <code>.m2</code> directory (like <code>settings-security.xml</code> in step 2). You either put it in <code>/home/jenkins/.m2/settings.xml</code> and it will be automatically used by all maven invocations, or put it somewhere else, but you will need to specify the path to this file with <code>-s</code> parameter. | ||
| + | |[[File:maven_inject_settings.png|800px]] | ||
| + | |- style="vertical-align:top;" | ||
| + | |5. It's required to add <code>--pinentry-mode loopback</code> as gpg argument in the pom.xml: | ||
<plugin> | <plugin> | ||
<groupId>org.apache.maven.plugins</groupId> | <groupId>org.apache.maven.plugins</groupId> | ||
| Line 50: | Line 61: | ||
</executions> | </executions> | ||
</plugin> | </plugin> | ||
| − | + | | | |
| + | |} | ||
'''Please note this is currently a workaround and will be improved in the future.''' | '''Please note this is currently a workaround and will be improved in the future.''' | ||
Revision as of 06:46, 5 October 2018
This page gives an overview of the build setup and infrastructure for EE4J projects.
Build infrastructure overview
Every EE4J project can request it's own Jenkins instance. All sub projects of a project share a single Jenkins instance.
All EE4J JIPPs will be hosted on CloudBees Jenkins Enterprise (CJE) / CloudBees Core infrastructure. Projects that still have a Jenkins instance on our old infrastructure will be migrated in Q4 2018. Jenkins instances running on ci.eclipse.org (e.g. https://ci.eclipse.org/grizzly) are currently hosted on the old infrastructure. Jenkins instances running on jenkins.eclipse.org (e.g. https://jenkins.eclipse.org/glassfish) are hosted on our new infrastructure (CJE/Core). Please note: the sub domains ci.eclipse.org and jenkins.eclipse.org will be unified at a later date.
Please see the EE4J Project Provisioning Status Google Doc for details.
How to requests a Jenkins instance?
Please file a bug file a bug against Eclipse Foundation > Community > CI-Jenkins to request your project's own instance. Make include the name of your project and ensure your project lead can +1 the request.
Deployment to OSSRH / Maven Central
Deploying artifacts to OSSRH (OSS Repository Hosting provided by Sonatype) requires an account at OSSRH. It is also required to sign all artifacts with GPG. The Eclipse IT team will set this up for the project.
Here are the required steps to configure your Jenkins build job for deployment to OSSRH:
Please note this is currently a workaround and will be improved in the future.