Notice: this Wiki will be going read only early in 2024 and edits will no longer be possible. Please see: https://gitlab.eclipse.org/eclipsefdn/helpdesk/-/wikis/Wiki-shutdown-plan for the plan.
Stardust/Knowledge Base/Integration/UI/UIMashup/Security Tokens Propagation For Eternal Web Applications
Purpose
This article describes how stardust propagates security tokens to external web applications. As well as where to set these tokens. This example uses implementation of both the LoginProvider and the DynamicParticipantSynchronizationProvider interface, based on Java property files.
Where To Set Session Tokens
In this example we have one class "org.eclipse.stardust.example.UserConfiguration" which is extending to "org.eclipse.stardust.engine.core.spi.security.ExternalUserConfiguration"
Below is the sample snippet where we are setting the security tokens:
@Override public Map<String, String> getSessionTokens() { String timeStamp = new SimpleDateFormat("yyyy.MM.dd.HH.mm.ss").format(new java.util.Date()); HashMap<String, String> sessionTokens = new HashMap<>(); sessionTokens.put("CustomAuthorization", "OAuth"); sessionTokens.put("oauth_token_secret", "Twitter Secret"); sessionTokens.put("oauth_signature_method", "RKD"); sessionTokens.put("TIMESTAMP: ",timeStamp); return sessionTokens; }
In this example we are using properties based synchronization provider. As per our implementation which we are using in this example you have to set below properties in "carnot.properties":
Security.Authentication.Mode = internal
Security.Authorization.SynchronizationProvider =org.eclipse.stardust.example.PropertyFileSynchronizationProvider
Verify Session Tokens
Whatever session token we have set in getSessionTokens() method these all will be fetched by "ippMashupAuthProxy.html" page and will be set as browser cookie before invoking to external web applications.
So logic for passing session tokens works like this:
1. When your Mashp Application acitivity in initialize if sessionTokens map is empty it directly invokes your external web application without looking up for "ippMashupAuthProxy.html" so in this case no cookie will set.
2. If sessionTokens map is not empty it looks up for "ippMashupAuthProxy.html" at same location where your mashp application is configured. Then this proxy page reads this map and set all the elements as browser cookies then invokes your actual web application
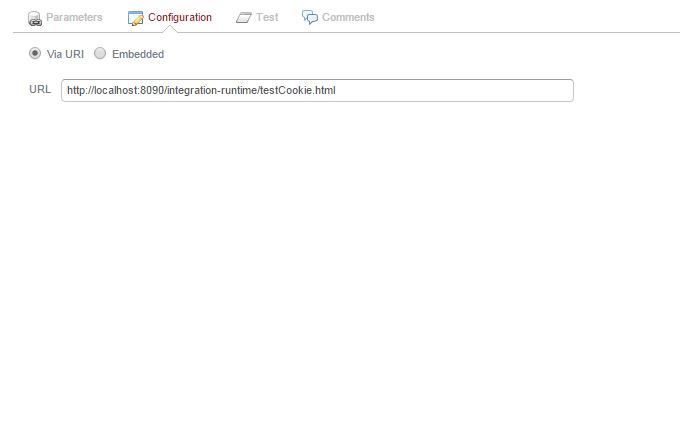
For example if MashUp application is configured to invoke http://localhost:8090/integration-runitme/testCookie.html then proxy page should also be deployed along it

Mashup Application configuration:
To verify if tokens are being propagated to Mashp Application i used one "testcookies.html" which will display all the cookies set in browser.
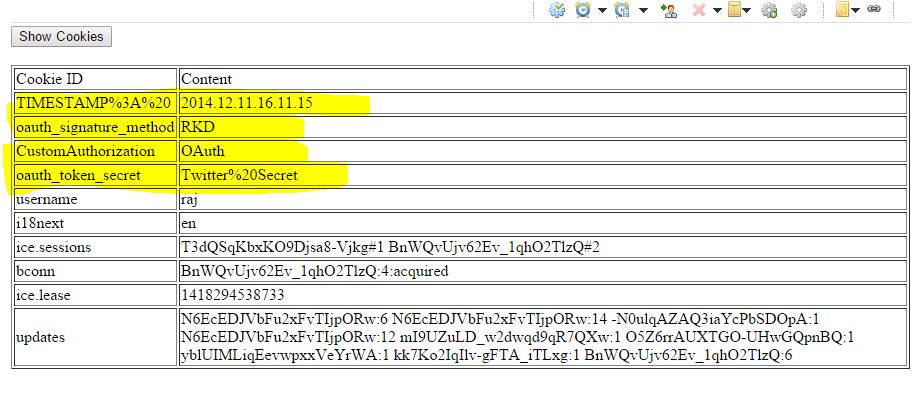
In the above screen you can see that whatever tokens we have set inside "getSessionTokens()" are available as browser cookies when mashp application is invoked
All the src code external web application and configuration files which we have discussed in this article could be found here Download Here