Notice: this Wiki will be going read only early in 2024 and edits will no longer be possible. Please see: https://gitlab.eclipse.org/eclipsefdn/helpdesk/-/wikis/Wiki-shutdown-plan for the plan.
RAP/Equinox Security Integration
| RAP wiki home | RAP project home |
Contents
Introduction
To ensure Eclipse is a secure runtime, enabling users and administrators to confidently work with the Eclipse client in environments where not all users and/or code sources are friendly. Providing integrated security functionality will allow Eclipse applications to protect their data, to authenticate and authorize valid users, and to protect against potentially malicious code packaged and distributed as plug-ins.
This will be done by enabling Java's standard security mechanisms within the Eclipse platform, defining new functionality where there are gaps in the available standard interfaces. Using Java's core standard interfaces will enable wider integration with code available throughout the Java community.
As Eclipse RCP has the same programming model as Eclipse RAP, we can adapt all the mechanisms that Equinox Security provides for our web application.
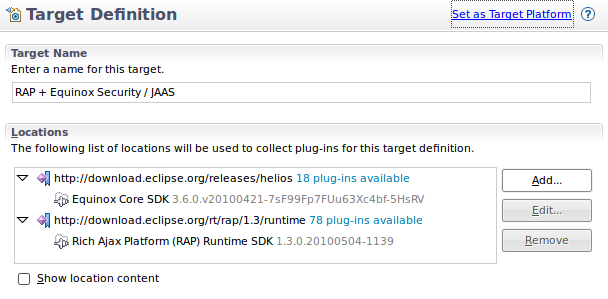
Target
The target setup is straight forward. All you need is a plain RAP runtime and the org.eclipse.equinox.security bundle. You can either create your own target platform or use the predefined target definition that is located in the org.eclipse.rap.security.demo project.
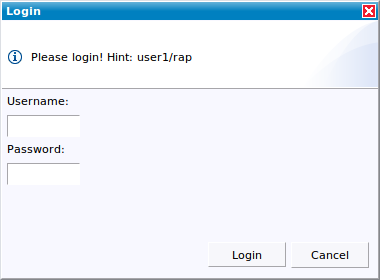
Login
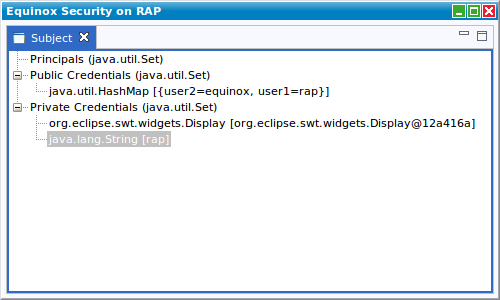
To use Equinox Security / JAAS for authentication, we have to prepare several things in our application.
Login Modules
The first thing is to pick a proper authentication mechanism for our scenario. This could either be LDAP, a Keystore or, as in the example, a hardcoded list of users. The LoginModule is responsible for checking the given credentials against it's source and tell if the authentication was successful. So the first step is to provide a JAAS config file to tell Equinox which login module we want to use.
DUMMY { org.eclipse.equinox.security.auth.module.ExtensionLoginModule required extensionId="org.eclipse.rap.security.dummy.dummyLoginModule"; }; UNIX { org.eclipse.equinox.security.auth.module.ExtensionLoginModule required extensionId="org.eclipse.rap.security.demo.unixLoginModule"; };
The configuration basically says that we want to use the ExtensionLoginModule which just acts as a proxy between JAAS and the Equinox Extension Registry. The real implementation here is defined by the extension (eg. org.eclipse.rap.security.dummy.dummyLoginModule, see plugin.xml).