Notice: this Wiki will be going read only early in 2024 and edits will no longer be possible. Please see: https://gitlab.eclipse.org/eclipsefdn/helpdesk/-/wikis/Wiki-shutdown-plan for the plan.
Difference between revisions of "Bandit STS/IdP Solution"
(→Details) |
(→See Also) |
||
| (7 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | {{#eclipseproject:technology.higgins}} | |
| − | [[ | + | '''NOTE: This page SHOULD follow [[Solution Description Template]]''' |
| − | == | + | == Introduction == |
| − | This | + | This solution deploys a system where a user can supply identity information to a relying party by selecting a [http://msdn2.microsoft.com/en-us/netframework/aa663320.aspx Windows CardSpace] card. The system assumes that the user is issued a managed card by the IdP. The issued card is imported into Windows CardSpace which is running on the client machine (Windows Vista or Windows XP with .NET3 installed). When the user visits a relying party he is presented with an option (a button, link, etc.) to select a CardSpace card to login. Upon selecting the option, the browser invokes Windows CardSpace, and the user is prompted to select a CardSpace card. If the user selects the managed card that was previously imported, Windows CardSpace will communicate with the Higgins STS to request a security token. These communications are done using the WS-* protocols. After a metadata-exchange, CardSpace sends an RST (request for security token) message to the Higgins STS. The RST contains information that tells the STS an IdAS context provider to connect to and how to authenticate to that context provider. The RST message also tells the STS what claim values are to be retrieved from the specified context provider in order to produce a security token. In this solution, the IdAS Context Provider is an LDAP provider which has been configured to retrieve information from an LDAP directory. |
| − | The components in this | + | == Developer Perspective == |
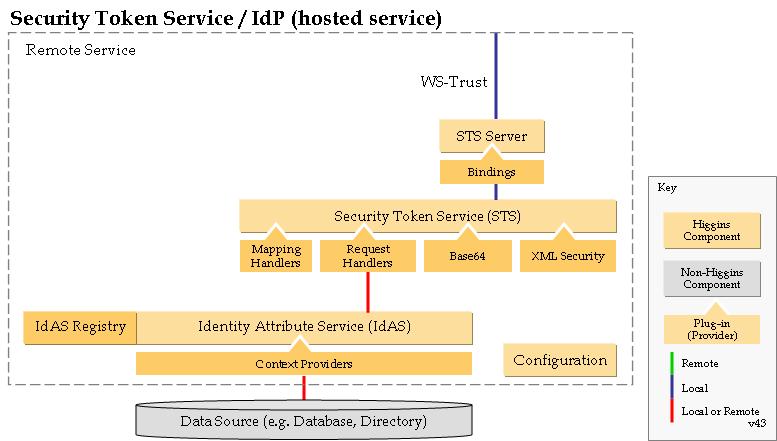
| + | === Architecture === | ||
| + | [[Image:deploy-sts-v43.JPG]] | ||
| + | |||
| + | The components in this solution, and their purpose are as follows: | ||
*Client Machine With CardSpace. This may be a Vista client or an XP client with .NET3 installed. This machine holds all of the CardSpace InfoCards for the user. It handles communications between the Higgins STS and the relying party. | *Client Machine With CardSpace. This may be a Vista client or an XP client with .NET3 installed. This machine holds all of the CardSpace InfoCards for the user. It handles communications between the Higgins STS and the relying party. | ||
| Line 33: | Line 37: | ||
|} | |} | ||
| − | + | ||
| − | + | ||
== Links == | == Links == | ||
| + | * http://code.bandit-project.org/trac/wiki/IdentityProvider <-- Novell Bandit site | ||
* [http://eclipse.org/higgins Higgins Home] | * [http://eclipse.org/higgins Higgins Home] | ||
Latest revision as of 13:47, 28 March 2009
{{#eclipseproject:technology.higgins}} NOTE: This page SHOULD follow Solution Description Template
Contents
Introduction
This solution deploys a system where a user can supply identity information to a relying party by selecting a Windows CardSpace card. The system assumes that the user is issued a managed card by the IdP. The issued card is imported into Windows CardSpace which is running on the client machine (Windows Vista or Windows XP with .NET3 installed). When the user visits a relying party he is presented with an option (a button, link, etc.) to select a CardSpace card to login. Upon selecting the option, the browser invokes Windows CardSpace, and the user is prompted to select a CardSpace card. If the user selects the managed card that was previously imported, Windows CardSpace will communicate with the Higgins STS to request a security token. These communications are done using the WS-* protocols. After a metadata-exchange, CardSpace sends an RST (request for security token) message to the Higgins STS. The RST contains information that tells the STS an IdAS context provider to connect to and how to authenticate to that context provider. The RST message also tells the STS what claim values are to be retrieved from the specified context provider in order to produce a security token. In this solution, the IdAS Context Provider is an LDAP provider which has been configured to retrieve information from an LDAP directory.
Developer Perspective
Architecture
The components in this solution, and their purpose are as follows:
- Client Machine With CardSpace. This may be a Vista client or an XP client with .NET3 installed. This machine holds all of the CardSpace InfoCards for the user. It handles communications between the Higgins STS and the relying party.
- Browser with extensions or plugins that can communicate with the local CardSpace. For IE, this must be IE7 or greater. For Mozilla, there is a plugin that must be installed.
- Server with Higgins STS and LDAP Context Provider (IdAS). The STS runs on this server as a Tomcat servlet using an Axis binding.
- Server with LDAP Directory. This server contains the LDAP directory server where the identity information is stored. NOTE: This can be installed on the same server as the STS, or a different server.
Deployment Notes
Higgins CardSpace Interop Deployment Notes
Details
| OS | Runtime | Binding | Open | URL | Owner |
|---|---|---|---|---|---|
| Open SUSE 10.2 | JVM 5.0 Tomcat 5.0 |
WS-Trust WS-Transfer |
TBD | Security Token Service | Daniel |
Links
- http://code.bandit-project.org/trac/wiki/IdentityProvider <-- Novell Bandit site
- Higgins Home